Features
Needs-based access control
Continuously clean up permissions, enable multi-cloud privileged access, and improve and accelerate compliance
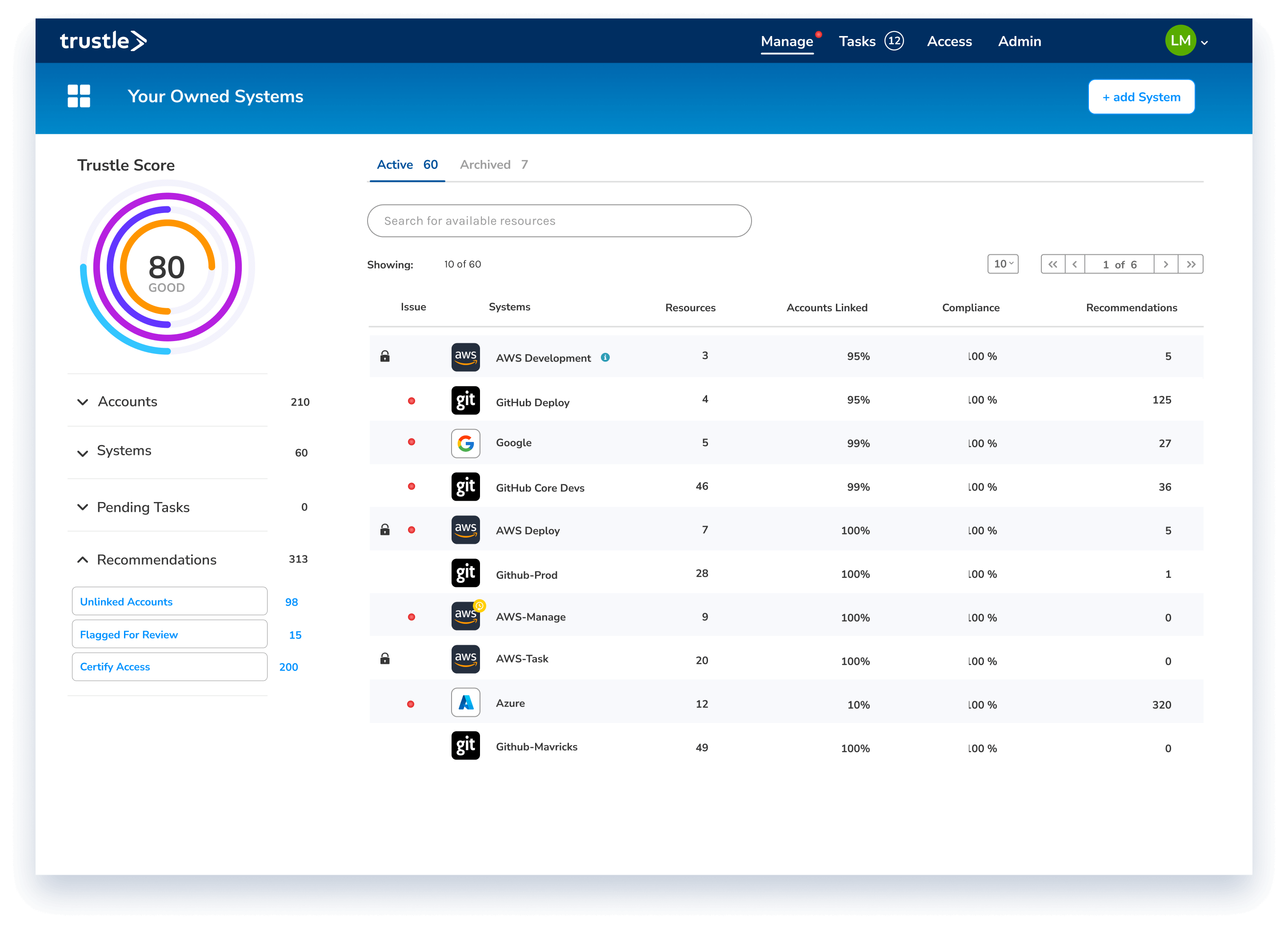
Securing the cloud environment
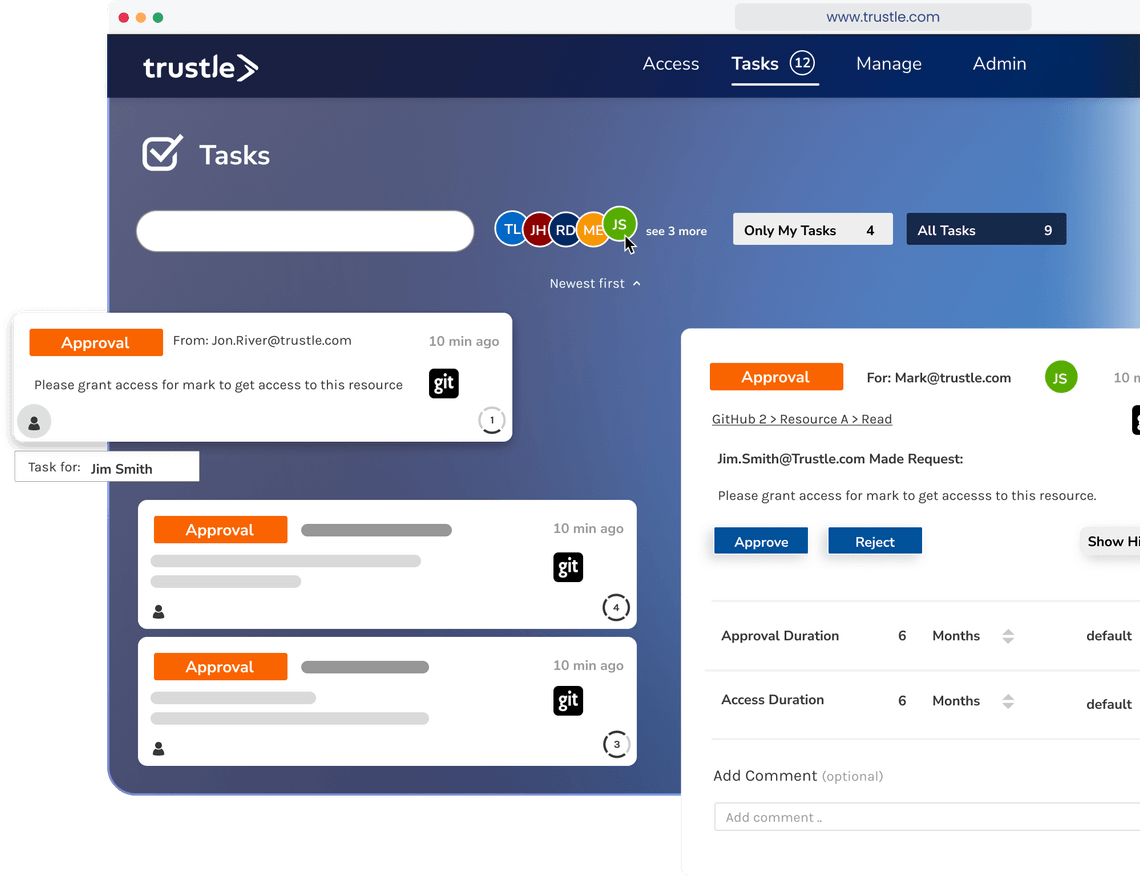
Trustle uses a unique blend of pragmatic and programmatic approaches to secure cloud systems. To support audit and regulatory requirements, Trustle provides approval workflows. For ongoing access activities, Trustle uses a combination approval status, risk score, and policy to determine the appropriate action. Of course, all of this activity is available as a history for certification and audit.
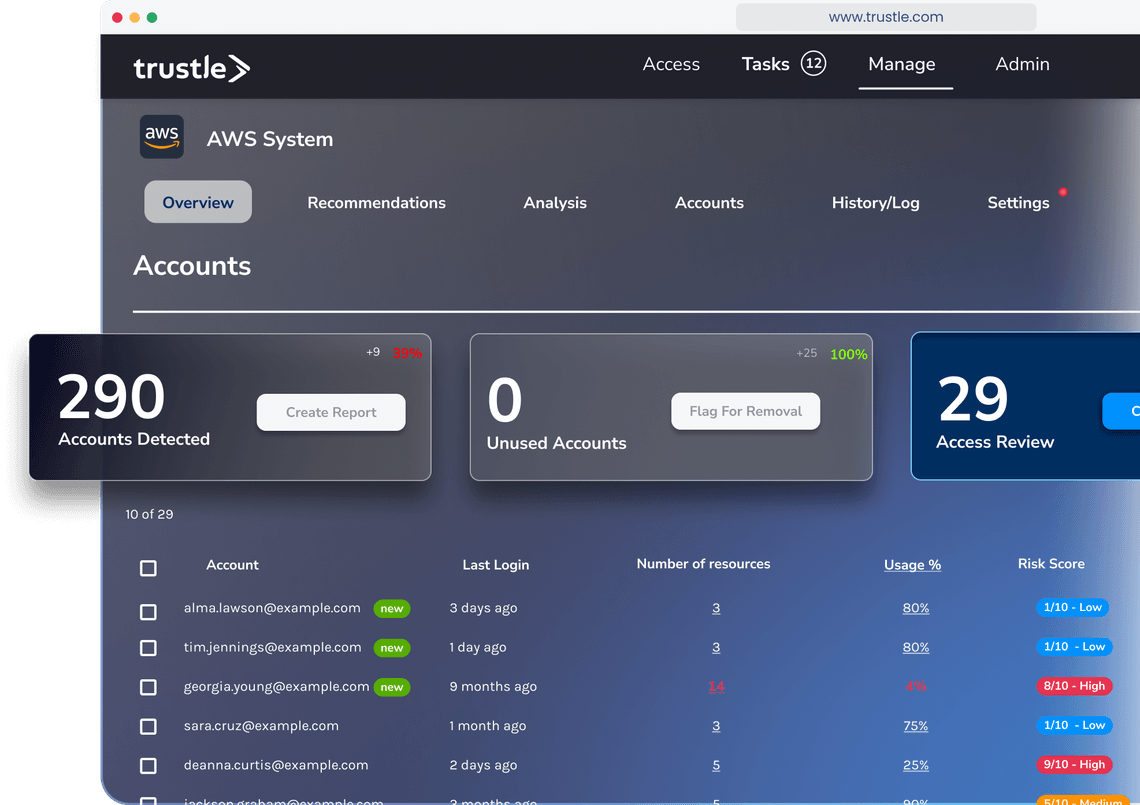
Cloud-native provisioning
Traditional provisioning products rely on approval & re-certification workflows, which often create more work with little security benefit. Trustle automatically identifies and removes access from cloud systems when not in use, and restores them through simple requests.
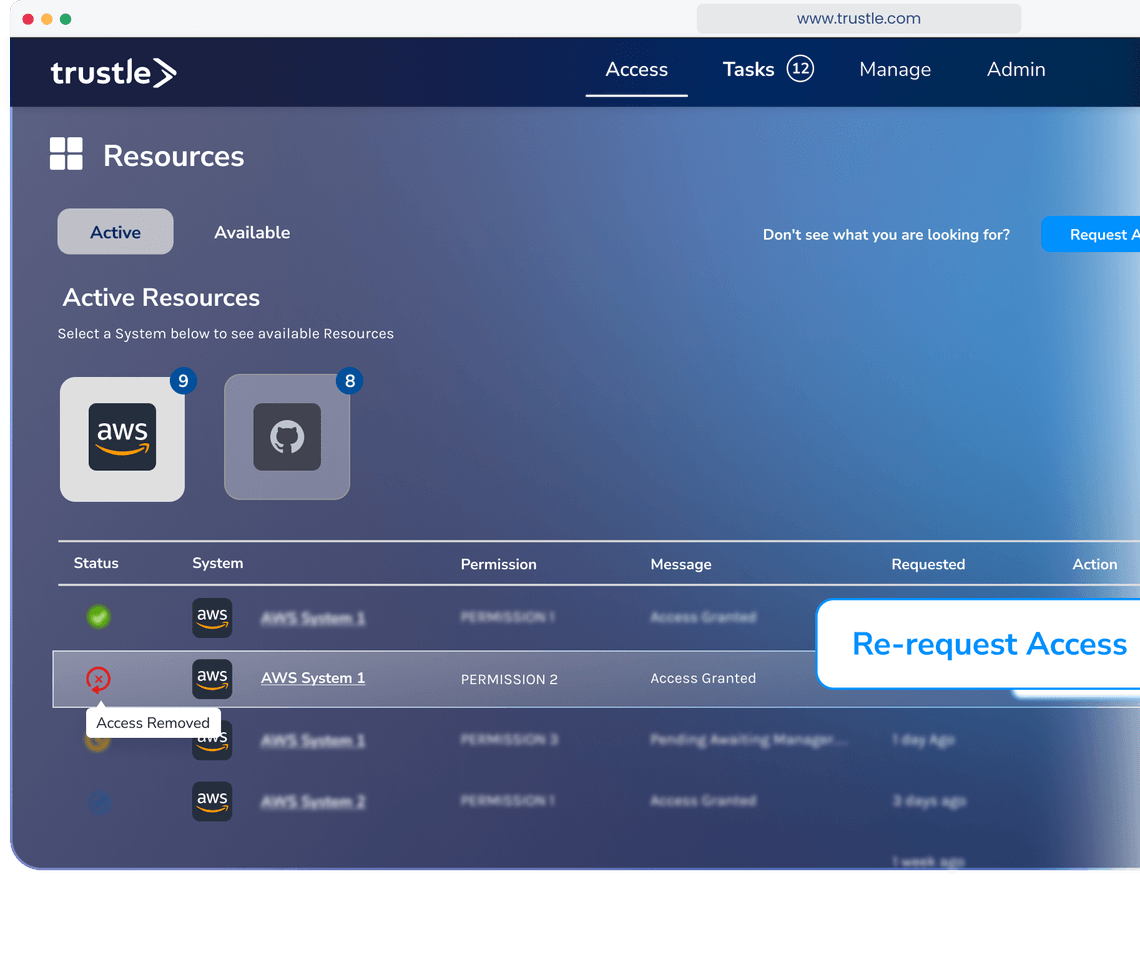
Native integration through APIs
Authorization engines require connected applications to support their proprietary APIs to talk to it. Trustle integrates natively with each cloud system to continuously configure appropriate access for each user account.
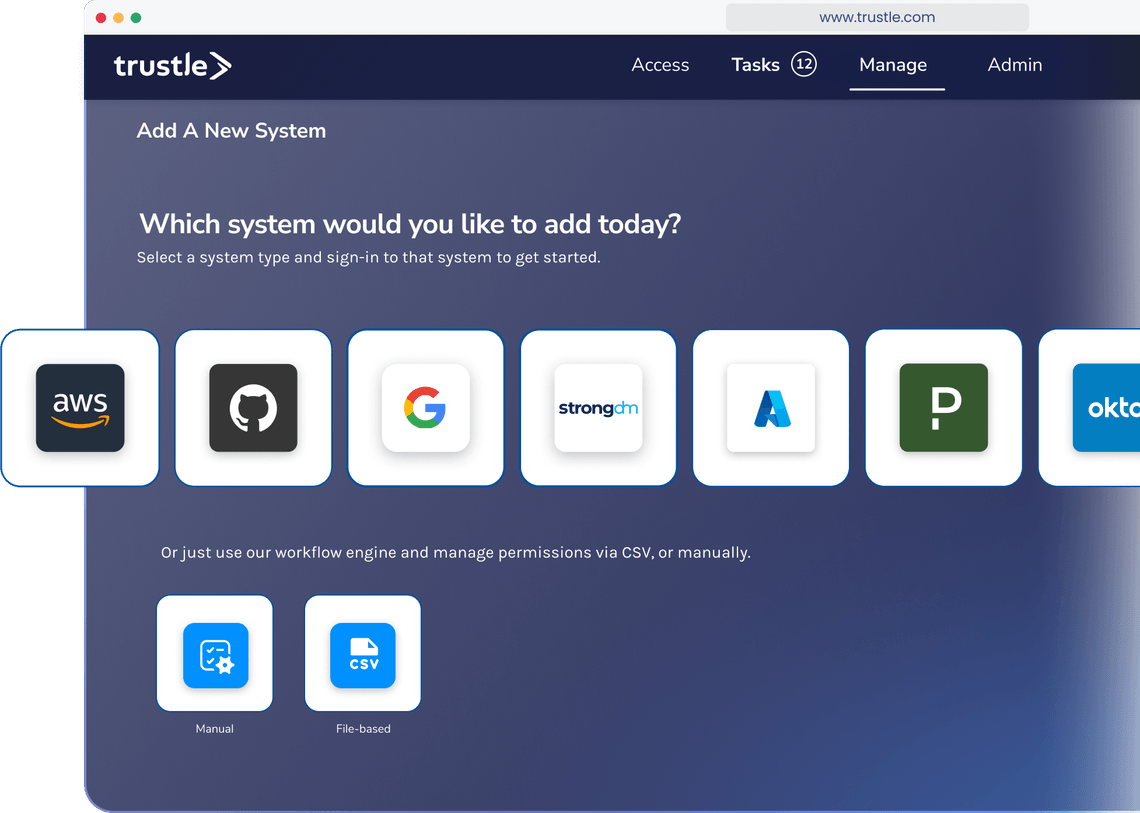
Access when you need it, and for how long you need it
Trustle’s policy-based + self-service model makes getting access simple for authorized users. Here are the steps:
Trustle also offers on-call features, so response teams can act with immediacy. Any team member on an on-call list (such as in PagerDuty) can immediately access any system and resource that is approved for that purpose.
- System owners build a catalog of resources, specifying the sensitivity of the resource
- Team members can request access to resources
- Depending on policy, a manager or system owner may need to approve the request and (optionally) change the default duration for access
- The team member instantly gains access
- Trustle removes access after it expires, but the team member can regain access upon request
Trustle also offers on-call features, so response teams can act with immediacy. Any team member on an on-call list (such as in PagerDuty) can immediately access any system and resource that is approved for that purpose.
Connect, compute, cleanup
Just-in-time access
Easily restore access that you’re already approved for
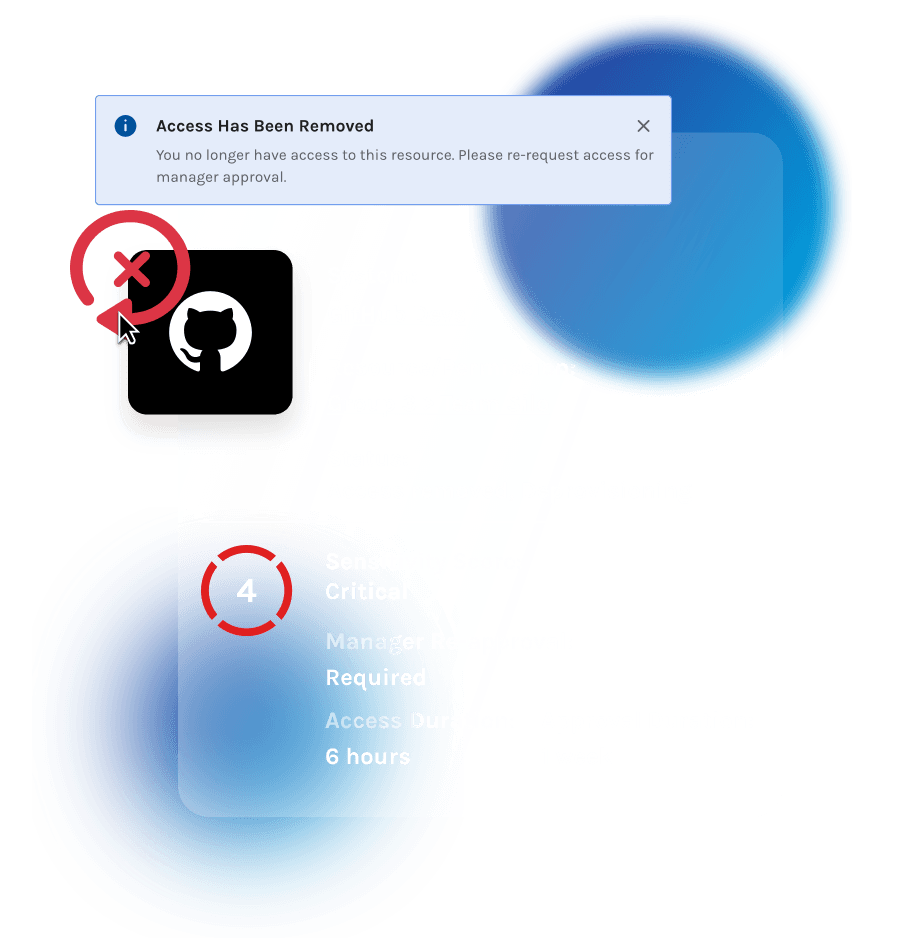
Automated access removal
Based on time and sensitivity of the resource
Visibility of all accounts and access
Overall Trustle score and drill-downs into access. Recommendations, and risk scores
Audit reporting
Create reports in any format of all the changes and approval chains of accesses to your cloud resources

Connect to the systems you use every day
Trustle connects through native APIs to keep your systems current with your access needs. We treat each system as its own particular security space, and we apply best practices, as well.
See all Integrations
 We spend three months and over $1M on user access certifications every year. With Trustle, our work is significantly reduced.
We spend three months and over $1M on user access certifications every year. With Trustle, our work is significantly reduced.
We spend three months and over $1M on user access certifications every year. With Trustle, our work is significantly reduced.
SVP, fixed income investing firm
Access for the right user, to the right resource, for the right length of time
Get Started for Free