Product
Timebound Access & Workflows
On the scale of access to everything and access to nothing, where does your company fall?
Trustle helps accelerate access reviews by allowing you to delegate the authority to trusted individuals within your organization who have the necessary context to approve or deny access. This empowers your access management solution to scale, while simultaneously empowering your employees to be more productive.
Trustle enforces zero standing privilege until least privileged, JIT access is required, ensuring your users only have the minimal access they need, when they actually need it. This helps minimize your attack surface, and reduces the risk of unauthorized access.
Trustle offers automation capabilities that allow you to automate routine tasks and workflows based on resource classifications, as well as previous access approval history. This saves valuable time and boosts productivity for your security teams, system owners, and access requestors.
Trustle automates on-call access, ensuring that engineers have the necessary access to resources during incidents. This reduces incident-related downtime, and keeps your on-call team at zero standing privilege until least privilege access is needed.
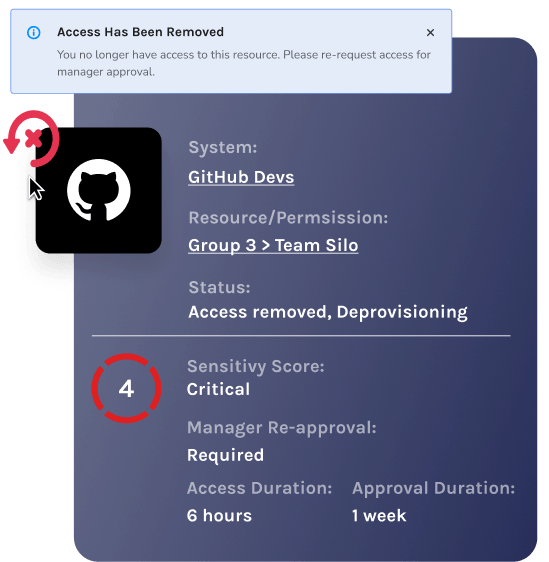
Trustle simplifies the process of revoking access to resources when an employee or contractor leaves your organization. This reduces the risk of unauthorized access and ensures the security of your data.
Just-in-time access
Easily restore access that you’re already approved for
Automated access removal
Based on time and sensitivity of the resource
Visibility of all accounts and access
Overall Trustle score and drill-downs into access.
Recommendations, and risk scores
Audit reporting
Create reports in any format of all the changes and approval chains of accesses to your cloud resources

As companies grow, how they manage their access must scale and evolve as well.
Where a non-secure, simple, one-size fits all approach may have worked in the beginning (spreadsheets sound familiar?), certifications compliance introduces a new layer of complexity to the process.
Resources now need to be classified and Roles need to be defined.
Employees, contractors, customers, and service accounts may all require unique approval workflows based on the sensitivity of the resource they are requesting access to.

Some companies develop internal, admin tools to try and support their growing business for compliance requirements. On one hand these internal systems may provide carte blanche access to internal, sensitive and non-sensitive data as requested, however on the other hand, they implement a rigid process which severely limits access and impacts productivity.
Modern enterprises have started to adopt several cloud-based applications, each with its own unique feature set and design platform. Maintaining the sprawl of these internal tools and the multitude of applications becomes a project all of its own.
Using native APIs, Trustle ingests account, permission, resource, and usage data from each of your cloud and SaaS systems. Using Trustle's machine learning technology, we provide deeper end-to-end visibility and control to each of your integrated systems.
Trustle empowers your team to make context based decisions providing compliant, automated access for the right user, to the right resource, for the right length of time.
Trustle offers an advanced, workflow solution that helps you efficiently and securely manage access to your cloud environment. You can set up Trustle's workflow to enforce your approval chain requirements and provide time-based access depending on the sensitivity of the resources being accessed.
You will know exactly who has access to what, And can trust your data is secure.
Trustle allows you to effortlessly scale permissions management in your enterprise by enforcing zero standing privilege until fine-grained, least privilege access is needed. This minimizes your attack surface by reducing the threat of stolen credentials.
Your tools don't need to change, but the overall adoption of least privilege access will.
Questions? Get In Touch
If you are just looking to ask us a quick question, feel free to send us an email at:
hello@trustle.com